The ISIS attack in Paris caused me to resurrect a paper I originally wrote for Rudy Giuliani’s Homeland Security Team in 2006. It introduced “resilience” into the presidential primaries…I added a couple of updates to make it more timely…
Terrorism is a battle for the mind. If ISIS falters, if it experiences defeats and appears to be weakening, it ceases to be a magnet for disenfranchised youths or wild-eyed zealots. If it is no longer revered and feared there is absolutely no hope of ever creating an Islamic Caliphate. Think about it in terms of gang violence, the Crips and the Bloods: “Nobody joins a gang that’s getting its ass kicked.”
This terrorist attack was predictable. It was a matter of saving face. The problem is that it wasn’t predictable with any degree of precision as to exactly where and when it would take place. But it was an absolutely Pavlovian response to losing ground in Syria.
The issue is “how do we respond?”
Setting the Context – 4th Generation Warfare[1] – ![Image647[1]](https://jmarke.files.wordpress.com/2015/11/image6471.jpg?w=170&h=215)
In January, 2002, one of Al-Qaeda’s leading strategists, ‘Ubed al-Qurashi, quoted extensively from two articles appearing in The Marine Corps Gazette stated categorically that the group was using 4GW or “4th Generation Warfare” against the United States – and expected to win[2].
Our enemy is sophisticated, he understands the evolution of warfare, and he reads our professional military journals. ‘Ubed al-Qurashi gives us an invaluable insight into the mind of our enemy. There is a blurring between the traditional battlefield (since the War of 1812 this battlefield has been located outside the United States), and transnational terrorism. That’s why our homeland security policy needs to reflect the tenants of 4GW warfare.
What is 4th Generation Warfare?
Warfare has evolved through four generations: 1) the use of massed manpower, 2) firepower, 3) maneuver, and 4) insurgency that employs all available venues —political, economic, social, technological and military—to convince opponents that their strategic goals are either unachievable or too costly.
“In Fourth Generation war, the state loses its monopoly on war. All over the world, state militaries find themselves fighting non-state opponents such as al-Qaeda, Hamas, Hezbollah, and the Revolutionary Armed Forces of Colombia. Almost everywhere, the state is losing. Fourth Generation war is also marked by a return to a world of cultures, not merely states, in conflict. We now find ourselves facing the Christian West’s oldest and most steadfast opponent, Islam.”(William Lind, Understanding Fourth Generation Warfare, Military Review, Sept -Oct. 2004)
Principles….the battle field has changed:
- They will seek to collapse our will to fight rather than destroying our physical ability to fight
- The battlefield will include the whole of our society.
- The battlefield is widely disperse, largely undefined with no geographic borders
- The distinction between military and civilian disappears
- The distinction between war and peace is blurred
- It is non-linear, i.e. 1+1 > 2, meaning a few dedicated attackers will produce asymmetrical effects out of proportion to their number
- Organizations are networked rather than hierarchical
- Cells in the global network do not need to be “managed” they self-organize
Fighting terrorists and fighting in foreign lands are very expensive propositions. It is physically, emotionally and financially debilitating. Vietnam and the Soviet occupation of Afghanistan proved that Western nations have little patience for the long haul. Terrorism works – at least some of the time. We withdrew from Lebanon after the Marine Barracks was bombed. And although contrary to its stated position, Israel has on numerous occasions negotiated with terrorists. But do jihadist terrorists even want to negotiate?
Bin Laden’s original fatwa called for three things: for the United States to leave Saudi Arabia, withdraw sanctions against Iraq, and withdraw support of Israel. When asked if he would call off his jihad if the United States withdrew from Saudi Arabia, bin Laden replied that he would not stop until the US stopped all aggressive acts against Muslims everywhere. Neither al Qaeda nor ISIS offer any room for negotiation…they basically want to redraw the map of the Middle East. A unifying theme for the jihadists is to end American and Western influence on Islamic countries and, ultimately the restoration of the caliphate. Whether or not this continues is debatable, but for not that is no room for compromise, and ISIS is ratcheting up the level of terrorism not only in the Middle East but elsewhere as well.
The recent attacks in Paris and in Los Angeles illustrate the fact that the battlefield is not contained by geo-political borders and that civilians are fair game for the terrorist; and, in fact, civilians are preferential targets. War is no longer a remote or abstract concept as gunmen and suicide bombers take the blood shed to our streets in Europe and America.
This is not the war of our fathers. It is not about blowing the hell out of things, body count or territory. It is about non-linearity, networks, and self-organized complexity. ISIS is a complex adaptive system – it is best understood in terms of complexity theory.

Non-linear behavior – two gunmen attack a public building in San Bernardino, California, killing 14 people. This incident ignited a heated debate over gun control, the immigration of refugees seeking asylum in the United States from war torn Syria, and political candidates urging that all Muslims be restricted from entering the United States. The investigation is tying up an enormous amount of federal and state law enforcement assets, all from two gunmen.
Networked v/s Hierarchical Behavior – There is a tacit assumption, at least in the United States military and law enforcement, that terrorism runs on a “command & control” and that events must be managed from the top down.
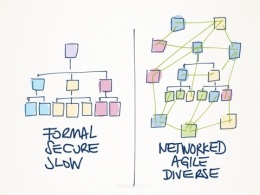
That was true of the German Army in World War Two, of the Iraqi Army in both Gulf Wars, and even of the Viet Cong. But today’s social media and 24×7 mobile technology gives rise to “agile and diverse” networks. Cells of terrorists exist in Paris, Baghdad, Aleppo and in Paris, Detroit, and Boston. They neither need nor respond well to command and control. By the way, do you know any social media savvy “20-somethings” that do?
Self-Organization – another tacit assumption by our leadership is that there must be an organization…there must be. Why? Well, because that is what we are taught at West Point and at the Harvard B School….how can anything be accomplished is there is no organization? And if the organization is obsolete, are managers also on the endangered spices list? The objective is to kill the Infidel – military or civilian. The extreme interpretation of the Koran legitimized, in fact, demands jihad. At lease al-Qaeda acted like a venture capitalist, reviewing terrorist plans and deciding whether or not to fund the proposed operation. We have empirical evidence that self-organization happens – maybe not all the time – but it does happen.
Scott Atran’s book “Talking with the Enemy” documents field interviews with active terrorists – leaders and rank and file. Scott Atran is an American and French anthropologist who is a Director of Research in Anthropology at the Centre National de la Recherche Scientifique in Paris, Senior Research Fellow at Oxford University in England, Presidential Scholar at John Jay College of Criminal Justice in New York, and also holds offices at the University of Michigan. He is a consummate professional who also took one hell of a lot of personal risks to conduct his field research spanning 20 years.
He focused on local interactions at the group level because that is precisely how this generation of terrorists works. I was struck by his description of “soccer buddies” and school mates evolving into terrorists, of buddies marrying each other’s sisters, and making jihad a family affair. And, most notably, this social structure makes it very difficult to gather human intelligence or compromise the group.
Yet these are not highly skilled or well trained terrorists They are armatures whose operations are crude and, (excuse the term) show “half-assed” planning and execution. The Paris attackers couldn’t get some of the suicide bomb vests to operate correctly. The San Bernardino”terrorists” couldn’t get their explosive devices to work at all, and attempted and failed to modify their semi-automatic rifles to full automatic. Yet the results were devastating. thank God they weren’t more competent!
Today’s terrorist need not be a rocket scientist or have the backing of a terrorist version of a venture capitalist. Pipe bombs and rifles (even a single shot shotgun will do in a pinch) are all that it takes. They are self-recruited and operate at the local level; and they are well versed in technology and every body has an iPhone. And they have achieved results far out of proportion to the time, effort and expense of the attack. They operate without strict supervision from “the top.” They are angry, often seeking revenge for actual or imagined affronts and legitimized -if not lionized – by their interpretation of the Koran.
So now what do we do?
4GW presents both cultural and political challenges to homeland security organizations. We like to prioritize targets, do cost-benefit analyses, finance tangible defenses, build walls at the Border. Those traditional approaches will not work in an environment characterized by high levels of complexity and uncertainty . Moreover non-nation state actors, e.g. ISIS, do not think or act like us. Taking the offensive with sheer military might will not destroy ISIS. Bullets cannot destroy an idea or an ideology. We obviously need to start with understanding our enemy – why do they do this and what do they want? But since that advice may fall on deaf ears, here are some immediate considerations.
Strategic Options
There are two security strategies in play to choose from that are fundamentally different:
- Resistance (favored by DHS, and based on doing things to prevent an attack or natural disaster, such as hardening a target to attack); and,
- Resilience (doing things to bounce back more effectively after an attack or natural disaster).
Resistance-Based Strategies
Resistance[3] strategies seek to keep danger away from the system in the first place. They are appropriate for dangers that can be planned for. Adjusting the building code to include earthquake grade rebar is a resistance strategy for buildings in an earthquake zone. Inoculation against a known infectious disease is a resistance based strategy. Camouflage is a resistance-based strategy, as in the federal witness protection program.
Resistance is a resource intensive strategy, i.e. it costs a lot of money to credibly defeat/prevent a terrorist attack. It is often focused on gadgets and technology. The resistance strategy is almost always focused across a narrow front or set of behaviors; and it is almost always static. Anti-virus software for your computer is a resistance strategy. By definition resistance strategies lack the ability to adapt and learn on the fly. Barriers, perimeter defense, the Great Wall of China and “defense in depth” are resistance-based strategies. But again, appropriate for known dangers, usually specific to a particular time and place. And they have their time and place in our portfolio.
The TSA screening process at airports is a resistance strategy. It works, more or less, and it eats up a lot of resources in the process. It, unfortunately, there are no alternatives, so lets not even argue about it. It is focused across a narrow front of scenarios and/or behaviors, i.e. preventing terrorists from gaining access to aircraft; or, if they slip by the screen, not having the tools of the trade to take over the aircraft, the last line of defense are sky marshals or passengers. TSA also has watch lists and has augmented the flight deck doors to be resistant to forced entry.
There is, by the way, no credible resilience strategy available to TSA in terms of passenger aircraft security, because once a plane is hijacked, the presumption is that it will either be blown up by the hijackers or used as a weapons platform to deliver a 9-11 type attack. “Bounce back” is not an option.
In 4GW the whole society as a potential target, where would one begin?
How could we physically secure all public buildings (for it is not just government buildings that are at risk)? Attacks can (and have) been made on restaurants, sporting events, concerts, schools, commercial office buildings, trains, bridges, the food supply, hospitals, and the list goes on. Further, the distinction between military and civilian targets is blurred. A military installation is no more likely than a retirement community to be a target, or a restaurant on a Friday evening in Paris. To paraphrase, Sun Tzu: “The more targets you have to defend the more diffuse you become and the more difficult it is to defend anything.”
A problem with many resistance strategies is a false sense of security they breed in the public. For example, the entrances to federal office buildings are usually staffed by 2 to 4 security officers (sharing one 38 cal. revolver). This defense, at best, is geared toward stopping a “lone gun” psycho bent shooting his supervisor. If terrorists come, they will be a war-fighting assault team wearing body armor and carrying main battle rifles loaded with 7.62mm full metal jacketed rounds. No private security guards or tactical police squads will be able to stand up to such massive firepower. Think about that the next time you walk through security in the Reagan Center, the Department of Commerce, or the Smithsonian.
Most of the time resistance-based defenses are ill-suited for waging 4GW and in combating terrorism. Once something is built (physically or, in the more abstract, in terms of doctrine or business model), the enemy can usually find a way to circumvent it.
Classic examples of resistance-based strategies that failed: the French Maginot line, Hitler’s Atlantic Wall, the Japanese defenses at Iwo Jima…each took years and millions to build, and each failed in hours. Remember, once the barrier is penetrated, it is essentially useless. As was the case with the Maginot Line, the Germans merely went around it, going through Belgium. It would have been far better for the French to spend their money on tanks as a mobile counter-force to counter Hitler’s Panzers than on set-piece forts that were quickly neutralized by the blitzkrieg.
Resilience-Based Strategies
Resilience-based strategies are ideal for coping with the complexity and fluidity of the 4GW battlefield. They work well when we are dealing with:
- high levels of uncertainty
- highly complex and inter-connected systems
- threats such as natural disasters, pandemics, terrorism, economic fluctuations, i.e. “fat tailed” threats characterized by low or unknowable probability and high consequence
Characteristics of resilience-bases strategies:
- Simple, flexible plans
- Contingencies – having many options on one’s hip pocket
- Hedging strategies (not putting all the eggs in one basket)
- Standard Operating Procedures (figuring out “who’s on first” before the hurricane hits)
- Fostering initiative
- Developing a common orientation, view point
- Driving responsibility down to the “field” operators, i.e. the shooters and responders
- Work for a variety of threats
We know the threat will take place, be it a terrorist attack, hurricane, earthquake, drought, food contamination threat, or pandemic…..we just don’t know when or where.
![baran_net[1]](https://jmarke.files.wordpress.com/2015/11/baran_net1.gif?w=352&h=264)
We begin to understand the threat by using network theory (actually setting up the problem as a series of nodes and lines) to get a visual sense of what’s going on. That way we can see critical paths and nodes, and begin to engineer redundancy into the network, so “taking out” several critical nodes won’t bring the whole thing crashing down. The theory of “scale free networks” (focusing on well connected nodes in the network and preferential attachment) addresses these issues around survivability to deliberate attacks.
Do you continually operate inside the red circle?
We have evolved a number of tools to deal with varying levels of uncertainty and complexity. However, and this is very important, we habitually use the wrong tools for the problem at hand. For example, “risk based” strategies that demand a probability be assigned to “quantify” the vulnerability of a terrorist target. Terrorist often falls into the upper right hand quadrant — wicked risks. (Graphic by John Marke)
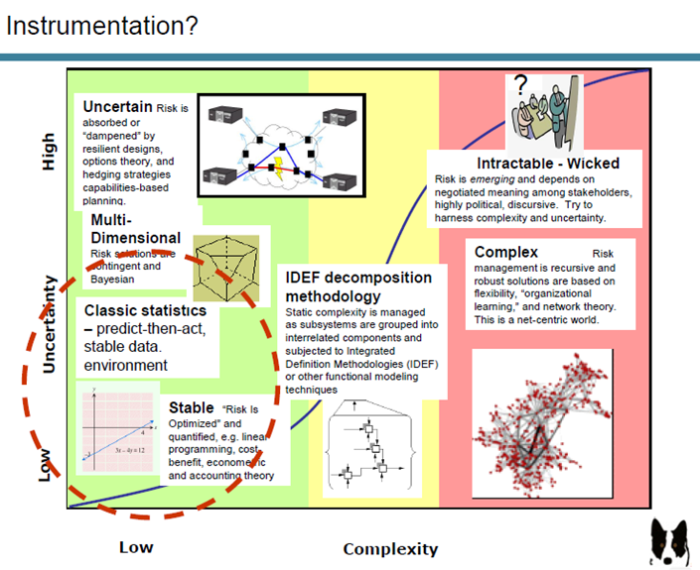
Characteristics of “wicked problems”…
- There is no definitive formulation of a wicked problem.
- Wicked problems have no stopping rule.
- Solutions to wicked problems are not true-or-false, but good or bad.
- There is no immediate and no ultimate test of a solution to a wicked problem
- Wicked problems do not have an enumerable (or an exhaustively describable) set of potential solutions, nor is there a well-described set of permissible operations that may be incorporated into the plan.
- Every wicked problem is essentially unique.
- Every wicked problem can be considered to be a symptom of another problem
- The planner has no right to be wrong (i.e., planners are liable for the consequences of the actions they generate).
“People, Ideas & Technology – In That Order” (Col John Boyd, USAF)
Resilience based strategies are first and foremost about people sharing a vision. Next comes ideas, i.e. how to innovate, organize, communicate, and operate together. Don’t look for a quick technological fix (which usually proves ineffectual in such complex systems).
Scale can be a resilience-based strategy, exemplified by the local-state-federal hierarchy that rests leadership at the lowest geopolitical level before escalation takes place. This only works when federal, state, and local leaders share the vision. This is especially important at organizational or geo-political boundaries…jurisdictional issues need to be hammered out and agreed upon well before the crisis takes place.
What are the organizational requisites for resilience-based strategies?
- Mutual trust and cohesion
- Intuitive feeling based on shared vision between all levels of command – this shared vision allows Marine Corps platoons to take independent action without having to talk to “central command.”
- Mission contract, generally considered a contract between superior and subordinate, i.e. my commander gives me the mission I am supposed to accomplish, how I accomplish it is my business as long as I stay within the rules of war and the mission parameters, and my commander will support me
- Schwerpunkt: Any concept that provides focus and direction to the operation
The focus is on the implicit. We are making progress! Today there are more examples of first responders swinging into action without explicit orders. Through a shared vision, understanding of the mission, and innate trust in their superiors, they will take the initiative.
The Author: A former Director at PwC and a lead in the Deloitte-Touche Federal Security Service John Marke consulted to the Department of Homeland Security on risk modeling and infrastructure vulnerabilities, the IRS, and the Department of Transportation. His civilian clients included GoldmanSachs, American Electric Power, and Harvard University. He is a former naval intelligence officer, cryptographer, and NCIS Agent.
Contact: 636-458-1917 or CTC8098@gmail.com
[1] Lind, William et al, “the Changing Face of war into the 4th Generation, “Marine Corps Gazette, Oct. 1989
[2] Hammes, TX, Fourth generation warfare Evolves, Fifth Emerges, Military review, May-June 2007
[3] A term used by P.H. Longstaff, Harvard University, Security, Resilience, and Communication In Unpredictable Environments (2004), I’m not really pleased with it but haven’t been able to come up with anything better.
![5102861494_bb05c450d2[1]](https://jmarke.files.wordpress.com/2015/11/5102861494_bb05c450d21.jpg?w=700)
![tsa-checkpoint1-300x200[1]](https://jmarke.files.wordpress.com/2015/11/tsa-checkpoint1-300x2001.jpg?w=344&h=229)
![isis-Paris-terror-attack-3[1]](https://jmarke.files.wordpress.com/2015/11/isis-paris-terror-attack-31.jpg?w=337&h=190)
![1_LE8JvU4Ca9ZOnTDI5l8MPQ[1]](https://jmarke.files.wordpress.com/2015/11/1_le8jvu4ca9zontdi5l8mpq1.jpeg?w=236&h=245)



Thanks for sending John. Very good analysis. I remember Bill Lind coming to speak with us when I was a captain studying at AWS. He is an odd guy but has a point w 4 GW. Tom Hammes and I served in 1/5 together and he is the one who set my son up with his agent when Tommy wrote his book – Rage Company. I was not aware Tom Hammes wrote on this subject but not surprised. He is a thinker and a good guy.
Snuffing this BS out all begins with Leadership and commitment. From there strategy and tactics can follow but this President admitted last year he didn’t have a strategy for ISIS and he isn’t demonstrating strength or leadership yet. From what we are seeing, whatever he has now isn’t working.
The Sunnis changed with the Anbar Awakening but our departure from Iraq left them hanging and I think allowed today’s ISIS to evolve. It’s brutal, effective and has our attention. The question is, is it too late for Europe. They say France has 10,000 radicalized Muslims. They need to use a war powers act, arrest them all, and send them to America on ships. The only logical thing for us to do would be to sink those ships in the middle of the Atlantic. Problem solved.
Hope all is well and hope you have a great Thanksgiving. I’m off to Tampa tomorrow for my Christmas tree business and will be back here in time for Christmas.
Tom Daly
Sent from my iPhone Please excuse any typos sent from my mobile device.
>